Security policies are provided in macOS to restrict which apps can run outside of the usual protective system policies. Here’s how macOS Sequoia can override system policies in some cases.
Apple’s macOS is renowned for its robust security features, making it one of the most secure operating systems available. However, like any system, it is not impervious to security breaches. Over the past decade, Apple has introduced a variety of security enhancements to bolster the safety of its macOS environment.
Some of the key security features that have been integrated into macOS include:
- Developer ID
- Gatekeeper
- App Notarization
- Digital app signatures
- System Integrity Protection (SIP)
Among these, Developer ID and Gatekeeper play crucial roles in verifying and authorizing applications on Mac systems. Gatekeeper is particularly significant as it prevents apps from running unless they are confirmed to originate from a registered Apple developer or the Mac App Store. This feature acts as a first line of defense against potentially harmful software.
Interestingly, apps that are Developer ID-verified can still run even if they are downloaded from outside the Mac App Store, provided they have been verified by Apple. This flexibility allows users to access a broader range of applications while maintaining a level of security.
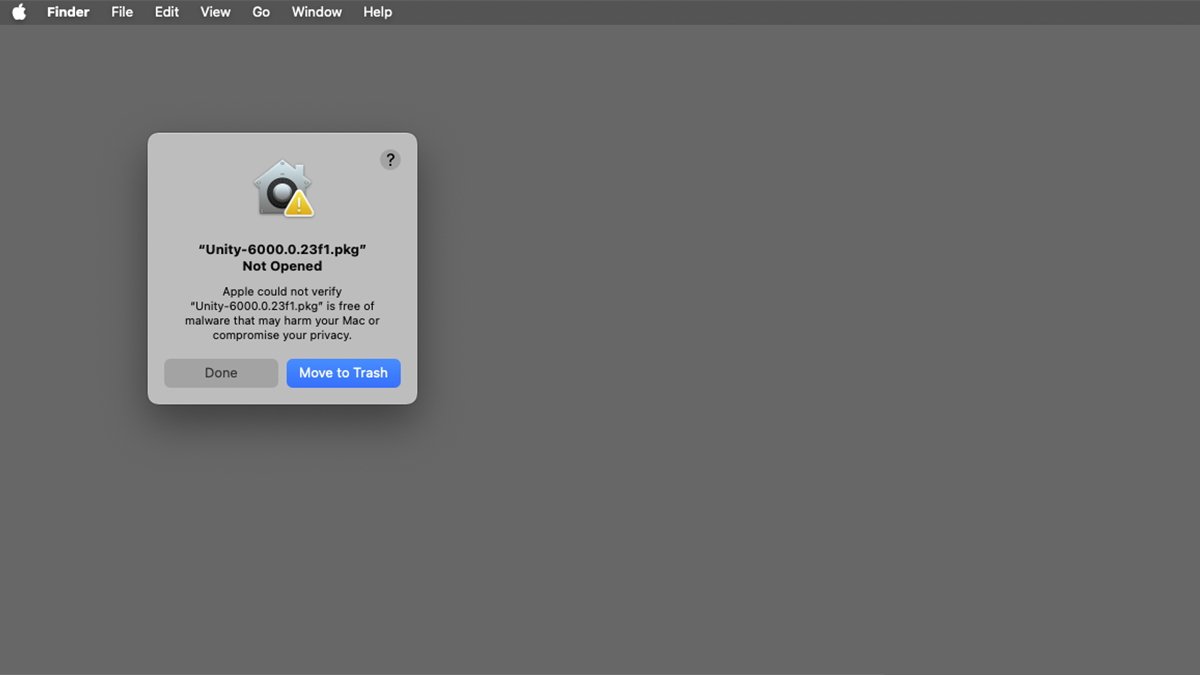
When you download a new app, you may notice a “Verifying” progress window in Finder. This is Gatekeeper in action, checking the signed digital receipts of all components of the app to ensure they are legitimate and safe to run.
Within the System Settings app, users can customize their security preferences. You can choose to allow only Gatekeeper-verified apps to run or enable apps from registered Apple developers via Developer ID. This customization empowers users to strike a balance between security and flexibility.
If you attempt to run an app that does not meet these security criteria, macOS will alert you that the app cannot be opened. To bypass this warning, you can click Done, navigate back to System Settings > Privacy & Security, and click the Open Anyway button.
App Notarization is another layer of security that Apple has implemented. This process ensures that apps and disk images are verified by Apple to confirm they do not contain malicious components, further safeguarding users from potential threats.
Digital app signatures provide an encrypted verification of a Mac app at the time of its creation by the developer. This signature guarantees that the app is authentic and that its contents have not been altered after distribution, adding another layer of trust for users.
System Integrity Protection (SIP) is a significant security feature that Apple introduced in macOS 10.11 El Capitan. SIP protects critical operating system files from being tampered with, even by the root UNIX user, as long as it is enabled. This feature is crucial for maintaining the integrity of the macOS environment.
While SIP can be disabled via the Terminal app, Apple strongly advises against doing so, as it exposes the system to various security risks.
Collectively, these security features are referred to as Runtime Protection in macOS, working together to create a secure environment for users.
Terminal Apps
In addition to the aforementioned features, Apple provides runtime protections for standalone binary apps that run through the Terminal app. These protections include extended attributes (xattrs) and other system-level safeguards.
However, some command-line Terminal apps may not be permitted to run under the default system security policies. This restriction is in place to protect users from unverified and potentially malicious third-party command-line tools.
It is important to note that these restrictions apply only to certain apps. In some instances, standard double-clickable macOS applications may require the execution of separate command-line tools or other software components.
Enabling Apps to Run Other Apps
If you wish to run an app that needs to operate outside of the macOS system security policies in macOS Sequoia, you can do so by revisiting the System Settings > Privacy & Security pane. Here, you will need to check each subpage for a switch that allows it.
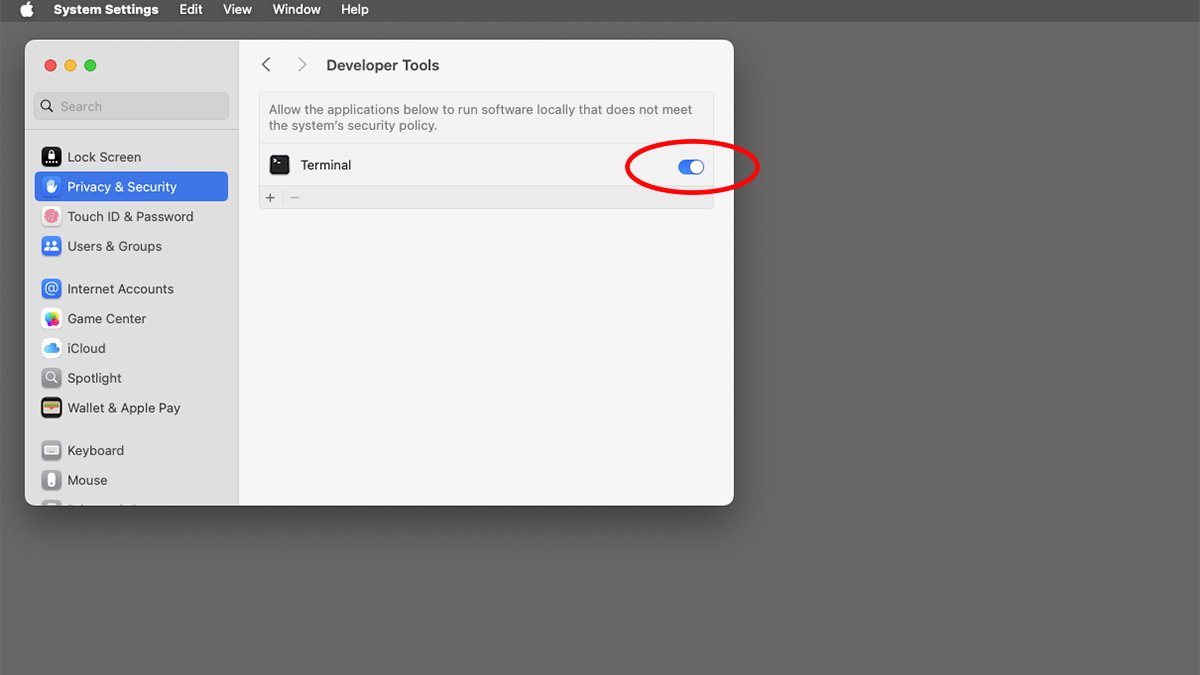
For instance, certain command-line developer tools may require permissions to run outside of the system security policies to execute other commands, process files, or perform restricted actions. To enable this, navigate to System Settings > Privacy & Security > Developer Tools and look for the relevant switch.
Currently, there is no option to enable this feature on a machine-wide basis, and it is likely for the best, as doing so could expose your Mac to additional security vulnerabilities. However, enabling this feature on an app-by-app basis is possible, provided the app in question supports it. This means you will need to check each app individually.
In most scenarios, users will not need to override macOS security policies. However, for specific applications and use cases, having the ability to do so can be beneficial.
For a comprehensive overview of Gatekeeper, Developer ID, and utilizing System Settings to open apps, refer to Apple’s Technote 102445, Safely open apps on your Mac.